In my experience as a tech enthusiast and system administrator, I’ve come to realize the importance of staying ahead of cybersecurity threats. It’s a constant battle to safeguard our customers’ sensitive data and systems from potential breaches. One of the common ways attackers try to gain access is through brute force attempts, where they repeatedly try different login combinations until they find the right one.
In a Windows environment, the Security event log records various security-related events, including logon attempts. Among these events, Event ID 4625 represents a failed logon attempt. By leveraging PowerShell, we can easily extract and analyze this data to identify potential brute force attacks.
The PowerShell Script
The following is the script we will be using:
Get-EventLog -LogName Security | Where-Object { $_.EventID -eq 4625 }
This one-liner script fetches the Security event log and filters it to only show events with Event ID 4625, which indicates a failed logon attempt.
Breaking Down the Script
Let’s break down the script step by step:
Get-EventLog -LogName Security: This command retrieves the Security event log from the local machine.|: The pipe symbol takes the output from the first command and passes it as input to the next command.Where-Object: This cmdlet filters the events based on specific criteria specified in the script block.{ $_.EventID -eq 4625 }: The script block within the Where-Object cmdlet checks if the EventID property of each event equals 4625, which indicates a failed logon attempt.
Understanding the Output
Once you run the script, it will display all the failed logon attempts recorded in the Security event log. To better read the output, you can modify script like limit the display to 100 lines and show only essential information, such as the username, time of the attempt, and the source IP. This way, you can quickly identify any suspicious activity without getting overwhelmed by unnecessary details.
Here’s an example of how I use it:
$FailedLogins = Get-EventLog -LogName Security | Where-Object { $_.EventID -eq 4625 }
$Counter = 0
$OutputFile = "FailedLogins.txt"
foreach ($Event in $FailedLogins) {
$UserName = $Event.ReplacementStrings[5]
$SourceIP = $Event.ReplacementStrings[19]
$EventTime = $Event.TimeGenerated
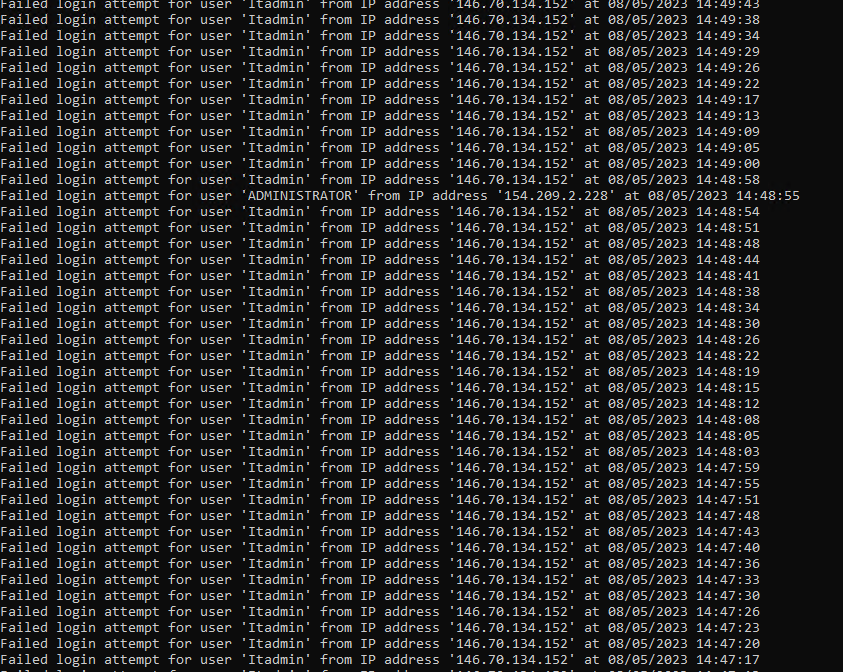
$Output = "Failed login attempt for user '$UserName' from IP address '$SourceIP' at $EventTime"
Write-Output $Output
$Output | Out-File -Append $OutputFile
$Counter++
if ($Counter -eq 100) {
$Counter = 0
Read-Host "Press Enter to continue..."
}
}
With this update, the script will write each failed login attempt to both the console and the “FailedLogins.txt” file. After displaying 100 lines in the console, it will prompt you to press Enter to continue displaying the next batch of 100 lines.
The “FailedLogins.txt” file will be created in the same directory where the script is executed, and each time you run the script, it will append the new failed login attempts to the existing text file. This way, you can keep a record of the failed login attempts for further analysis and reference.
Here’s the output:
Taking Action
Identifying failed logon attempts is a crucial step in the security process, but it doesn’t end there. It is essential to investigate further and take appropriate action based on the findings. Depending on the organization’s security policies, you may need to:
- Investigate: Review the failed logon attempts to determine if they are isolated incidents or part of a larger attack pattern.
- Implement Account Lockout Policies: To combat brute force attacks, consider enforcing account lockout policies that temporarily lock out accounts after multiple failed login attempts.
- Modify Your Firewall or ACLs: Use geolocation to block regions where you have no users or customers. Start or update a blacklist which ensures that known malicious addresses are automatically blocked, preventing repeat offenders from causing any harm.
- Monitor Regularly: Schedule the script to run at regular intervals and implement alerts or notifications to quickly respond to suspicious activity.
Conclusion
Of course, the script is just one part of our overall cybersecurity strategy. It’s essential to have other security measures in place and maintain a proactive approach to protect our systems continuously. Still, this PowerShell script has become an indispensable tool in our arsenal, giving us peace of mind knowing we can quickly respond to failed login attempts and keep our sensitive data safe. With the power of automation, we can confidently face the ever-evolving world of cybersecurity threats.